 vRealize产品家族包含了运维监控、日志分析和云服务平台等组件,不仅可以帮助企业提升信息化服务效率,还可以降低故障发生。2015年我开始专注云服务、自动化和信息化流程集成的相关内容,本次通过替换vRealize产品证书,来进一步提升使用体验。
vRealize产品家族包含了运维监控、日志分析和云服务平台等组件,不仅可以帮助企业提升信息化服务效率,还可以降低故障发生。2015年我开始专注云服务、自动化和信息化流程集成的相关内容,本次通过替换vRealize产品证书,来进一步提升使用体验。
VMware Realize产品家族包含如下常用产品:
- vRealize Operations
- vRealize Log Insight
- vRealize Network Insight
- vRealize Automation
- vRealize Lifecycle Manager
- vRealize Identity Manager
企业根CA和中间CA的搭建,请参考 [企业CA系列一]搭建企业根CA和中间CA
警告:一定要预先在测试环境进行验证,并考虑好相关联的系统证书信任问题!
前提条件和操作步骤概述
vRealiz系列产品的证书替换均非常简单,推荐替换顺序如下:
- 替换vRealize Operations证书
- 替换vRealize Log Insight证书
- 替换vRealize Network Insight证书
- 替换vRealize Automation 7.x iaas证书
- 替换vRealize Automation 7.x appliance证书
- (vRA8)替换vRealize Lifecycle Manager证书
- (vRA8)替换vRealize Identity Manager证书
- (vRA8)替换vRealize Automation 8.x证书
- 如果替换了vCenter和NSX-T的证书,需要在vRealize系列产品中重新连接,并添加证书信任
准备证书目录和cfssl证书配置文件
鉴于本篇文章涉及替换的证书过多,再加上通过前面几篇文章,大家已经对证书签发和替换有了一定的熟悉度,所以,我们将概述介绍证书签发过程。
首先,我们准备相关产品证书目录,如下所示:
/root
/ca
/intermediate
/corp
/certs
/corp
/mgmt-vrops.corp.local
/config.json
/mgmt-vrops-csr.json
/mgmt-vrli.corp.local
/config.json
/mgmt-vrli-csr.json
/mgmt-vrni.corp.local
/config.json
/mgmt-vrni-csr.json
/mgmt-vra7.corp.local
/config.json
/mgmt-vra7-csr.json
/mgmt-iaas.corp.local
/config.json
/mgmt-iaas.corp.local
/mgmt-vrlcm.corp.local
/config.json
/mgmt-vrlcm-csr.json
/mgmt-vdim.corp.local
/config.json
/mgmt-vidm-csr.json
/mgmt-vra8.corp.local
/config.json
/mgmt-vra8-csr.json然后,我们为每一个产品准备 config.json和mgmt-xxx-csr.json文件,config.json都是相同的,mgmt-xxx-csr.json文件需要根据每个产品的域名和IP地址进行修改,下面以vRealize Operations Manager产品为例。 针对每个vRealize产品需要修改mgmt-xxx-csr.json文件的以下内容:
- CN": "mgmt-vrops.corp.local"(修改为服务器域名)
- "hosts": ["127.0.0.1","mgmt-vrops","mgmt-vrops.corp.local","192.168.100.51"] (修改为服务器的主机名、域名和IP地址)
- "expiry": "87600h" (证书有效期为10年)
cd /root/certs/mgmt-vrops.corp.local
cat <<EOF > /root/certs/mgmt-vrops.corp.local/config.json
{
"signing": {
"default": {
"usages": ["digital signature","key encipherment","signing","server auth"],
"expiry": "87600h"
}
}
}
EOF
cat <<EOF > /root/certs/mgmt-vrops.corp.local/mgmt-vrops-csr.json
{
"CN": "mgmt-vrops.corp.local",
"hosts": [
"127.0.0.1",
"mgmt-vrops",
"mgmt-vrops.corp.local",
"192.168.100.51"
],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"L": "Changchun",
"O": "VMware",
"OU": "DevOps",
"ST": "Jilin"
}
]
}
EOF
[可选]vRA8多租户证书建议
当您的企业计划采用vRA8的多租户时,推荐采用通配符证书,这样可以省去每次添加租户重新替换证书的时间。 下面是vRA8通配符证书的mgmt-vra8-wildcard-csr.json参考配置:
* CN": "vRA8 Wildcard Certificate"(证书的通用名)
* "hosts": ["127.0.0.1","*.corp.local","*.mgmt-vra8.corp.local","192.168.100.60","192.168.100.61"] (*.corp.local用于vIDM多租户证书,*.mgmt-vra8.corp.local用于vRA8多租户证书,192.168.100.60和192.168.100.61为vIDM和vRA8的IP地址)
* "expiry": "87600h" (证书有效期为10年)cat <<EOF > /root/certs/mgmt-vra8-wildcard/mgmt-vra8-wildcard-csr.json
{
"CN": "vRA8 Wildcard Certificate",
"hosts": [
"127.0.0.1",
"*.corp.local",
"*.mgmt-vra8.corp.local",
"192.168.100.60",
"192.168.100.61"
],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"L": "Changchun",
"O": "VMware",
"OU": "DevOps",
"ST": "Jilin"
}
]
}
EOF通过中间CA为vRealize系列产品签发证书
# vROPS
cd /root/corp-ca/certs/mgmt-vrops.corp.local
cfssl gencert -ca=/root/intermediate/corp/corp-intermediate-ca.pem -ca-key=/root/intermediate/corp/corp-intermediate-ca-key.pem -config=config.json mgmt-vrops-csr.json | cfssljson -bare mgmt-vrops
cat mgmt-vrops.pem mgmt-vrops-key.pem ../../intermediate/corp/corp-intermediate-ca.pem ../../ca/root-ca.pem > mgmt-vrops-chain.pem
# vRlI
cd /root/corp-ca/certs/mgmt-vrli.corp.local
cfssl gencert -ca=/root/corp-ca/intermediate/corp/corp-intermediate-ca.pem -ca-key=/root/corp-ca/intermediate/corp/corp-intermediate-ca-key.pem -config=config.json mgmt-vrli-csr.json | cfssljson -bare mgmt-vrli
cat mgmt-vrli.pem mgmt-vrli-key.pem ../../intermediate/corp/corp-intermediate-ca.pem ../../ca/root-ca.pem > mgmt-vrli-chain.pem
# vRNI
cd /root/corp-ca/certs/mgmt-vrni.corp.local
cfssl gencert -ca=/root/corp-ca/intermediate/corp/corp-intermediate-ca.pem -ca-key=/root/corp-ca/intermediate/corp/corp-intermediate-ca-key.pem -config=config.json mgmt-vrni-csr.json | cfssljson -bare mgmt-vrni
cat mgmt-vrni.pem ../../intermediate/corp/corp-intermediate-ca.pem ../../ca/root-ca.pem > mgmt-vrni-chain.pem
# vRA7
cd /root/corp-ca/certs/mgmt-vra7.corp.local
cfssl gencert -ca=/root/corp-ca/intermediate/corp/corp-intermediate-ca.pem -ca-key=/root/corp-ca/intermediate/corp/corp-intermediate-ca-key.pem -config=config.json mgmt-vra7-csr.json | cfssljson -bare mgmt-vra7
cat mgmt-vra7.pem ../../intermediate/corp/corp-intermediate-ca.pem ../../ca/root-ca.pem > mgmt-vra7-chain.pem
cat mgmt-vra7-key.pem mgmt-vra7.pem ../../intermediate/corp/corp-intermediate-ca.pem ../../ca/root-ca.pem > vra-chain-key.pem
# iaas
cd /root/corp-ca/certs/mgmt-iaas.corp.local
cfssl gencert -ca=/root/corp-ca/intermediate/corp/corp-intermediate-ca.pem -ca-key=/root/corp-ca/intermediate/corp/corp-intermediate-ca-key.pem -config=config.json mgmt-iaas-csr.json | cfssljson -bare mgmt-iaas
cat mgmt-iaas.pem ../../intermediate/corp/corp-intermediate-ca.pem ../../ca/root-ca.pem > mgmt-iaas-chain.pem
# vLCM
cd /root/corp-ca/certs/mgmt-vrlcm.corp.local
cfssl gencert -ca=/root/corp-ca/intermediate/corp/corp-intermediate-ca.pem -ca-key=/root/corp-ca/intermediate/corp/corp-intermediate-ca-key.pem -config=config.json mgmt-vrlcm-csr.json | cfssljson -bare mgmt-vrlcm
cat mgmt-vrlcm.pem ../../intermediate/corp/corp-intermediate-ca.pem ../../ca/root-ca.pem > mgmt-vrlcm-chain.pem
# vIDM
cd /root/corp-ca/certs/mgmt-vidm.corp.local
cfssl gencert -ca=/root/corp-ca/intermediate/corp/corp-intermediate-ca.pem -ca-key=/root/corp-ca/intermediate/corp/corp-intermediate-ca-key.pem -config=config.json mgmt-vidm-csr.json | cfssljson -bare mgmt-vidm
cat mgmt-vidm.pem ../../intermediate/corp/corp-intermediate-ca.pem ../../ca/root-ca.pem > mgmt-vidm-chain.pem
# vRA8
cd /root/corp-ca/certs/mgmt-vra8.corp.local
cfssl gencert -ca=/root/corp-ca/intermediate/corp/corp-intermediate-ca.pem -ca-key=/root/corp-ca/intermediate/corp/corp-intermediate-ca-key.pem -config=config.json mgmt-vra8-csr.json | cfssljson -bare mgmt-vra8
cat mgmt-vra8.pem ../../intermediate/corp/corp-intermediate-ca.pem ../../ca/root-ca.pem > mgmt-vra8-chain.pem
替换vRealize Operations Manager证书
- 登录vRops Admin管理控制台;https://mgmt-vrops.corp.local/admin
- 点击,右上角第二个SSL证书图标
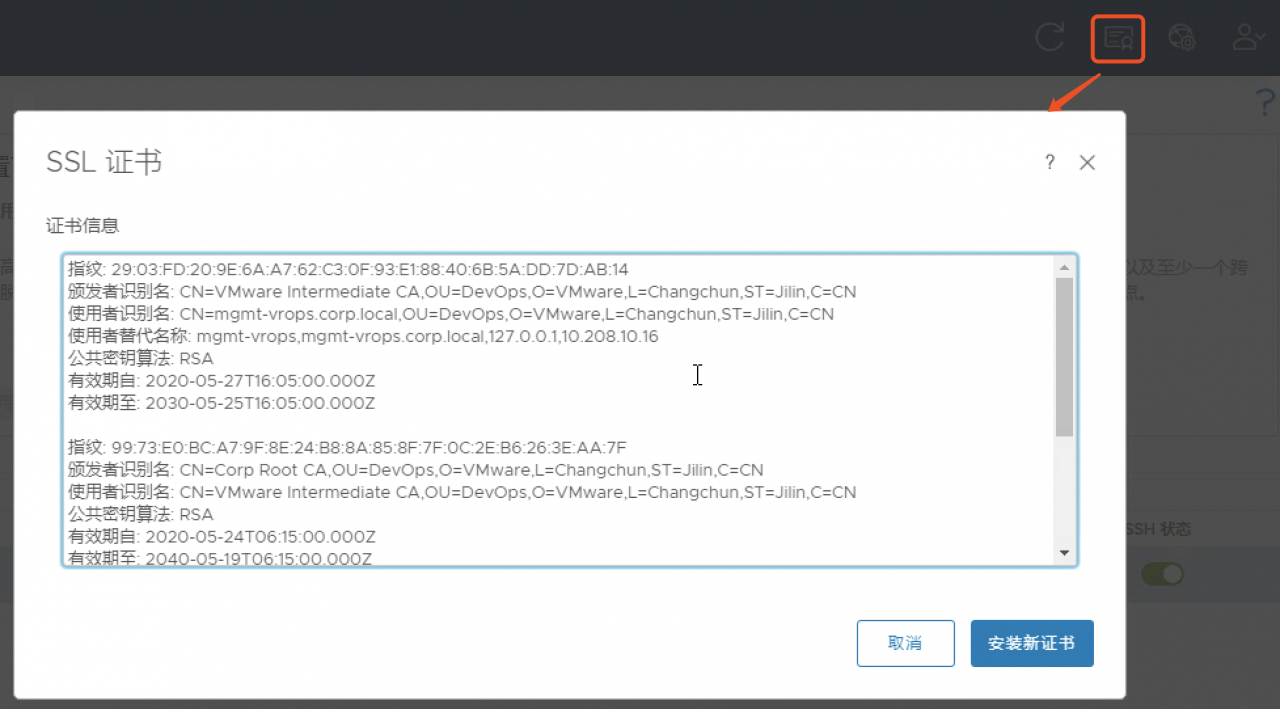
- 安装新证书->浏览->mgmt-vrops-chain.pem->安装
- 服务重启完毕后,证书替换完成
替换vRealize Log Insight证书
- 登录vRli管理控制台
- 系统管理->SSL->选择文件->mgmt-vrli-chain.pem->保存
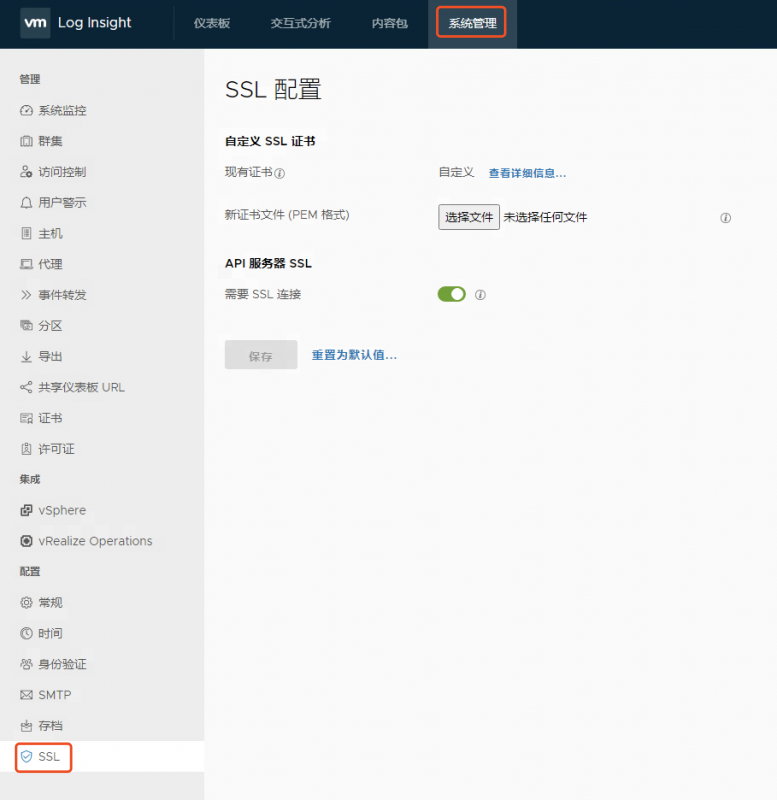
- 服务重启完毕后,证书替换完成
替换vRealize Network Insight证书
- ssh登录到vRNI虚拟机,用户名:consoleuser 密码:
- 运行custom-cert list查看是否有自定义证书,如果有,使用custom-remove删除
- 从远程主机导入证书
custom-cert copy --host mgmt-vault.corp.local --user root --port 22 --path /root/corp-ca/certs/mgmt-vrni.corp.local/mgmt-vrni-cert-chain.pem
custom-cert copy --host mgmt-vault.corp.local --user root --port 22 --path /root/corp-ca/certs/mgmt-vrni.corp.local/mgmt-vrni-key.pem
- 应用证书
custom-cert apply- 等待UI服务重启完毕,证书替换完成
替换vRealize Automation 7.x证书
vRealize Automation 7.x的证书包含三个:
- IaaS Web和Manager Service(共用一个证书)
- vRA
- vRA Appliance(5480)
- 登录vRealize Automation Appliance管理页面;https://mgmt-vra7.corp.local:5480
- vRA->Certificates->IaaS Web->mgmt-iaas-chain.pem and mgmt-iaas-key.pem->Save Settings
- RSA Private Key=mgmt-iaas-key.pem
- Certificate Chain=mgmt-iaas-chain.pem
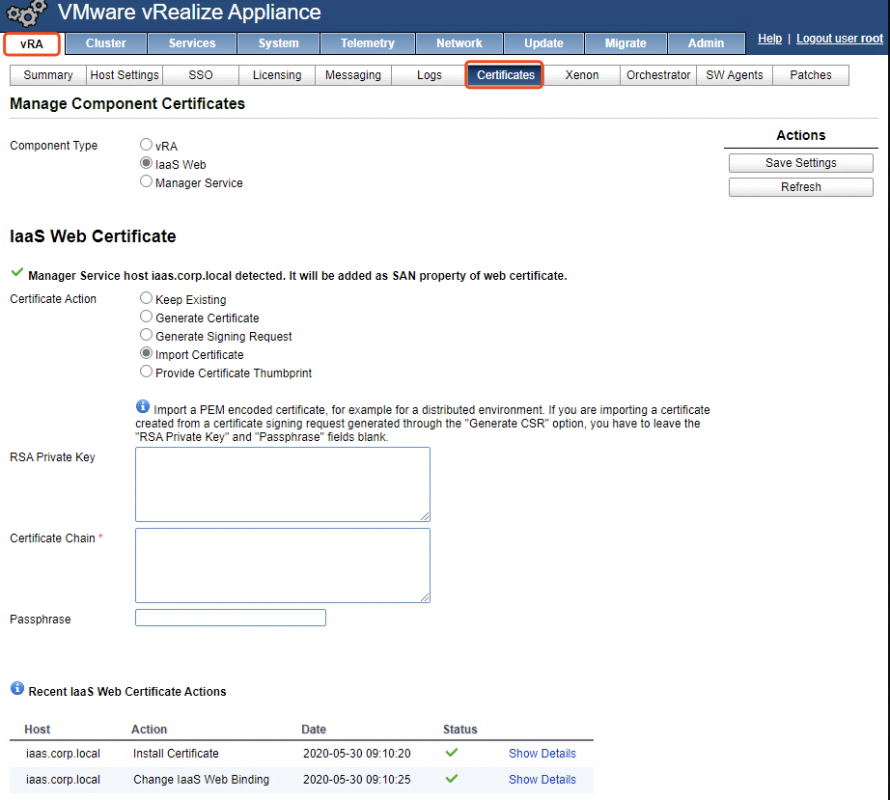
- vRA->Certificates->vRA->mgmt-vra7-chain.pem and mgmt-vra7-key.pem->Save Settings
- 通过SSH登录到vRA7 Appliance中,替换管理设备证书
ssh [email protected]
mv /opt/vmware/etc/lighttpd/server.pem /opt/vmware/etc/lighttpd/server.pem-bak
scp [email protected]:/root/corp-ca/certs/mgmt-vra7.corp.local/mgmt-vra7-chain.pem /opt/vmware/etc/lighttpd/server.pem
service vami-lighttp restart
service haproxy restart
- vRA7证书替换完成
替换vRealize Lifecycle Manager证书
- 通过SSH登录到vRLCM中,替换server.cert和server.key为企业中间CA签发证书,并添加企业根CA、中间CA到系统的受信任证书存储中。
cd /opt/vmware/vlcm/cert
# backup certificate.
mv server.crt server.crt.old
mv server.key server.key.old
scp [email protected]:/root/corp-ca/certs/mgmt-vrlcm.corp.local/mgmt-vrlcm-chain.pem ./server.cert
scp [email protected]:/root/corp-ca/certs/mgmt-vrlcm.corp.local/mgmt-vrlcm-key.pem ./server.key
# copy root and intermediate ca.
scp [email protected]:/root/corp-ca/ca/root-ca.pem .
scp [email protected]:/root/corp-ca/intermediate/corp/corp-intermediate-ca.pem .
# add root and intermediate ca to photon os trust store.
cat corp-intermediate-ca.pem >> /etc/pki/tls/certs/ca-bundle.crt
cat root-ca.pem >> /etc/pki/tls/certs/ca-bundle.crt
/usr/bin/rehash_ca_certificates.sh
# restart nginx service
systemctl restart nginx
- vRLCM证书替换完成
替换vRealize Identity Manager和vRealize Automation 8.x证书
在vRA8.x环境中,VIDM和vRA8的证书都是有vRealize Lifecycle Manager进行集中管理的,替换过程非常简单。
- 登录vRealize Lifecycle Manager控制台
- 进入到Locker页面
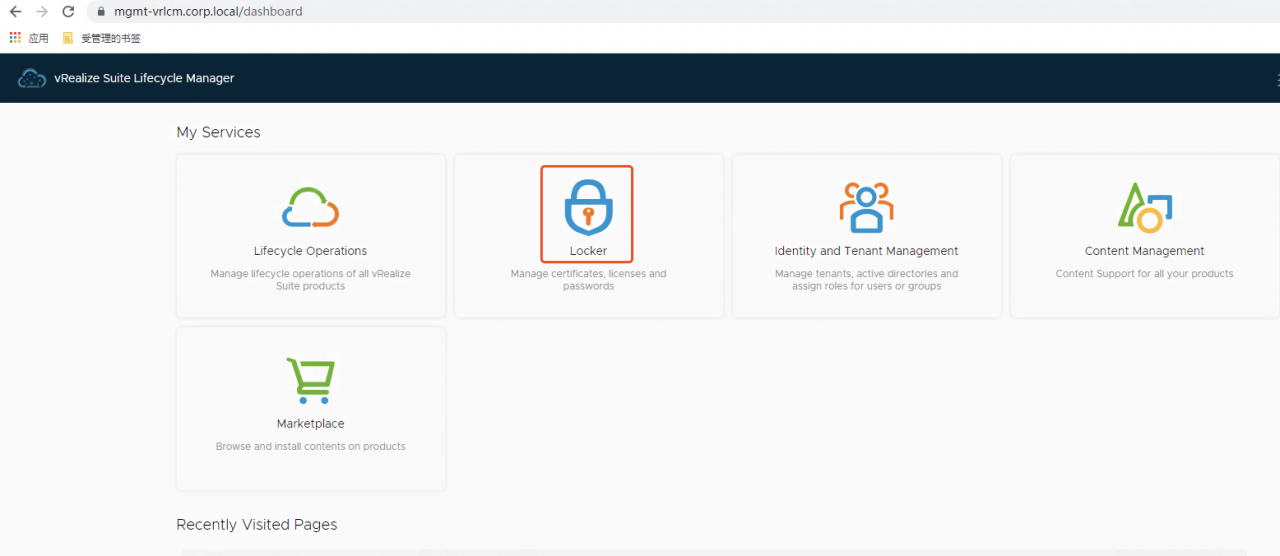
- Certificate->IMPORT
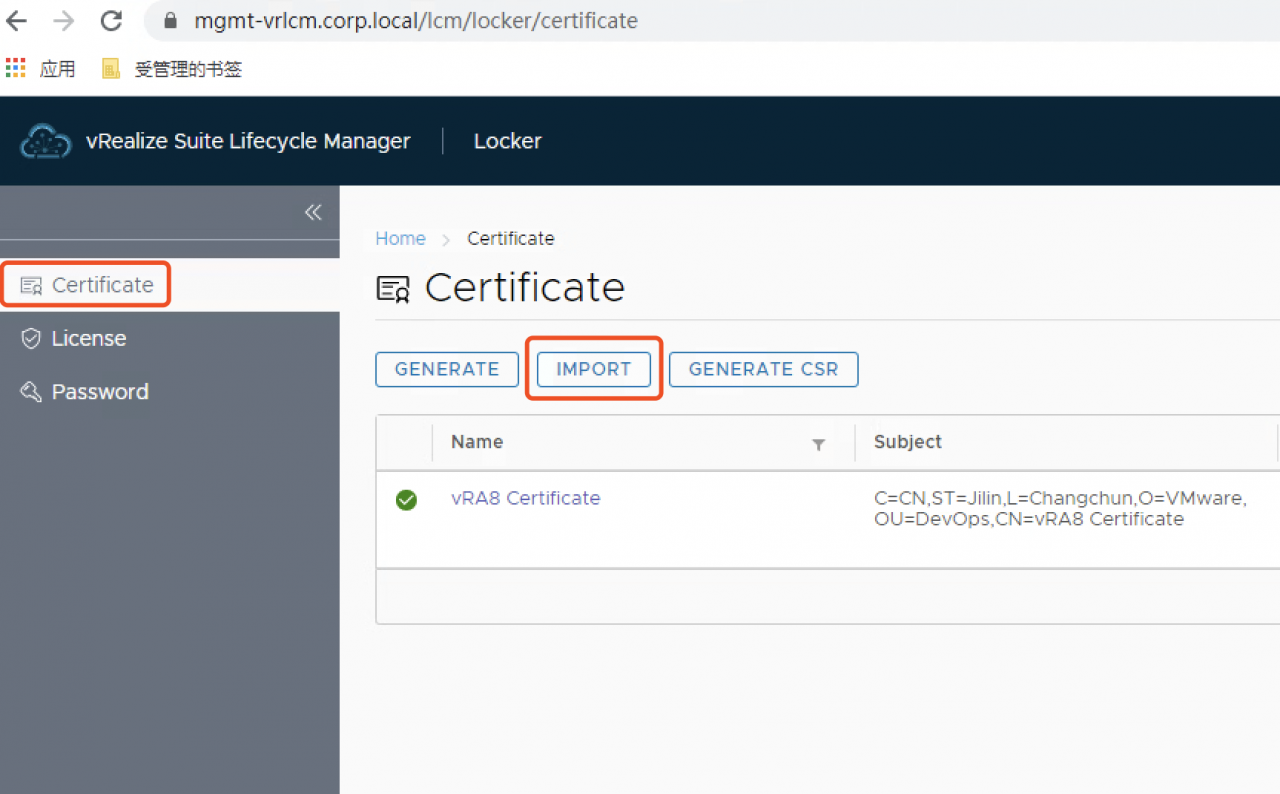
- 输入vIDM证书名字和信息,点击"IMPORT"导入证书
- Name=vIDM Certificate
- Priviate Key=mgmt-vidm-key.pem
- Certificate Chain=mgmt-vidm-chain.pem
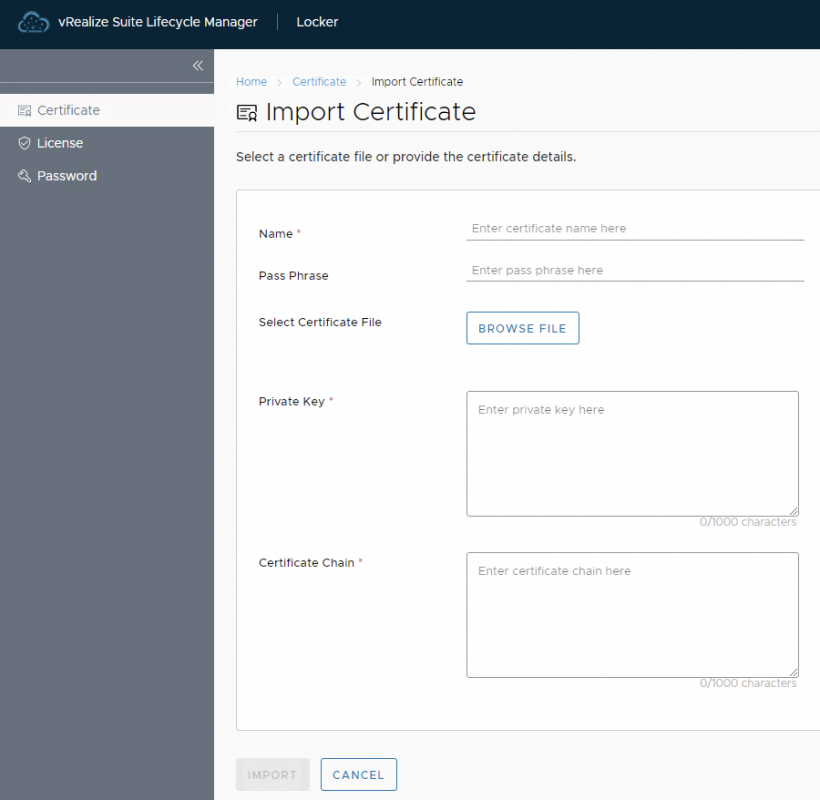
- 重复3-4步,导入vRA8证书
- 进入"Lifecycle Operations"管理页面
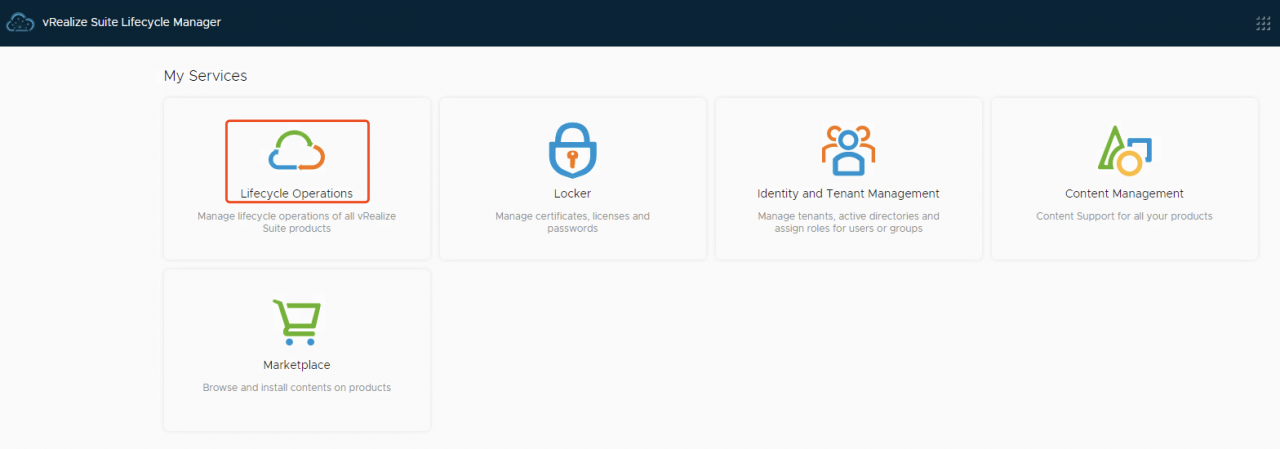
- Environments->vIDM->VIEW DETAILS
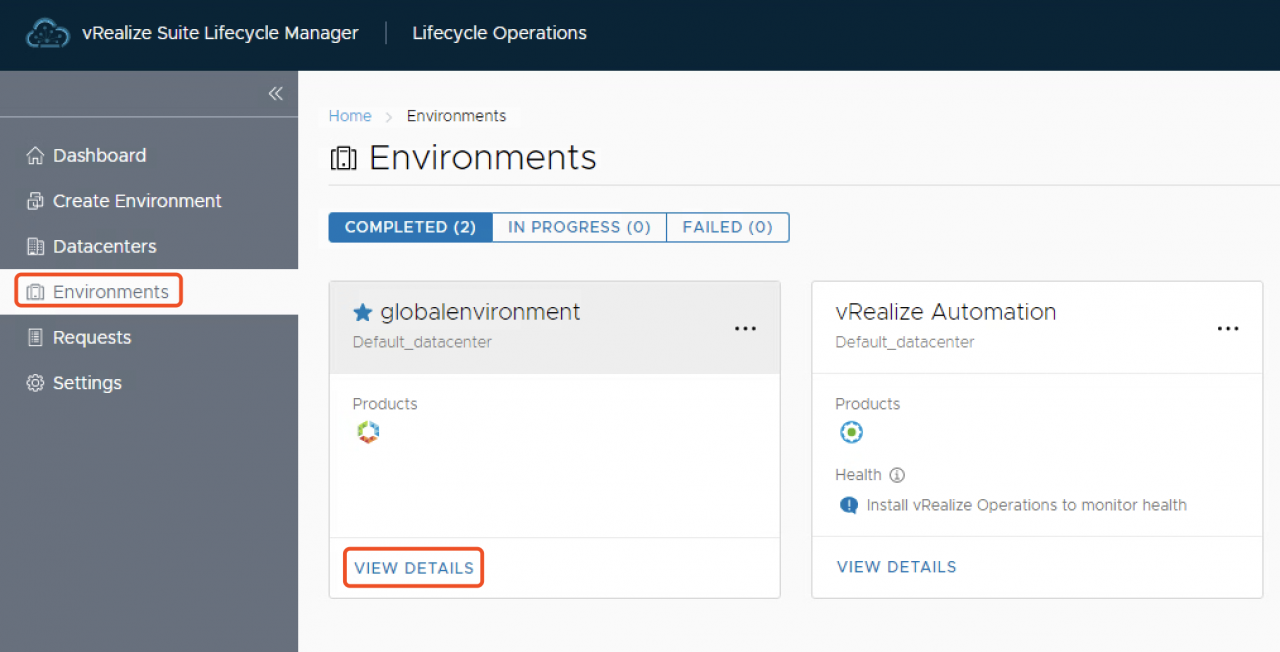
- VMware Identity Manager更多->Replace Certificate
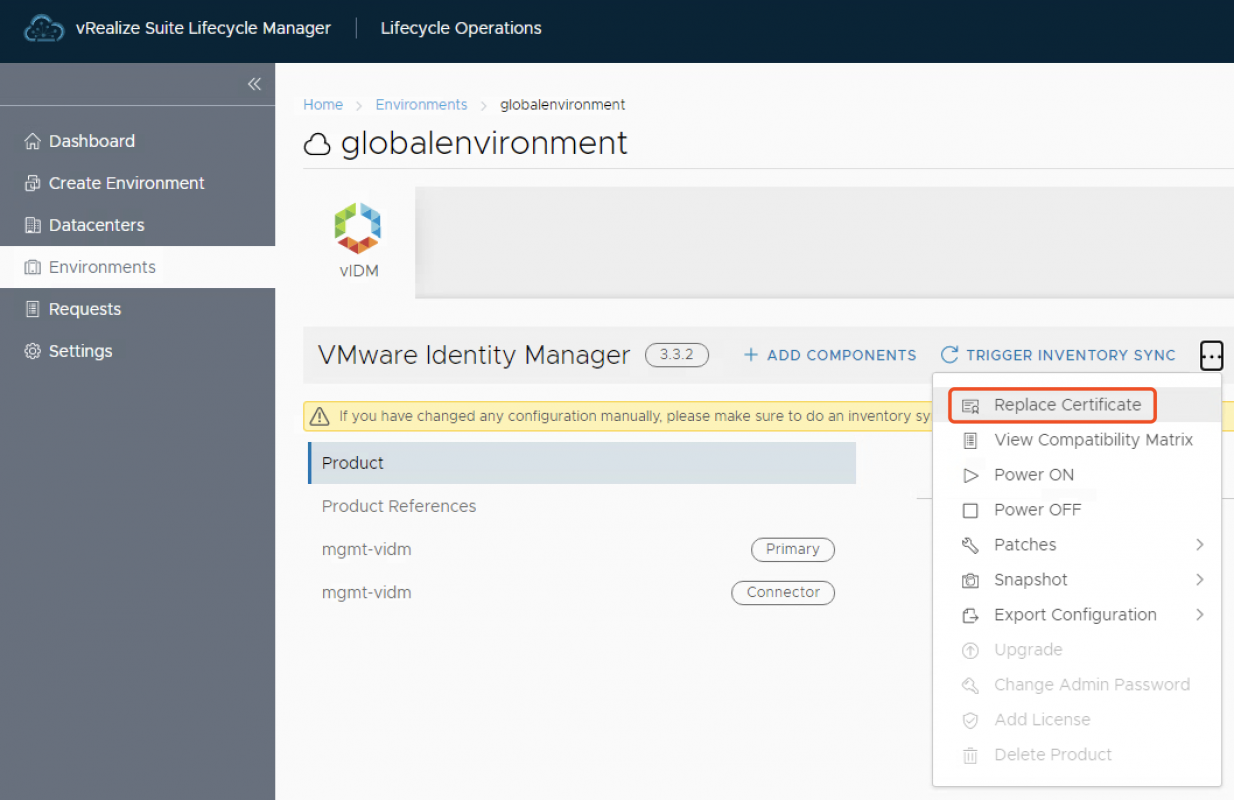
- 在2.Select Certificate中,选择导入的vIDM证书
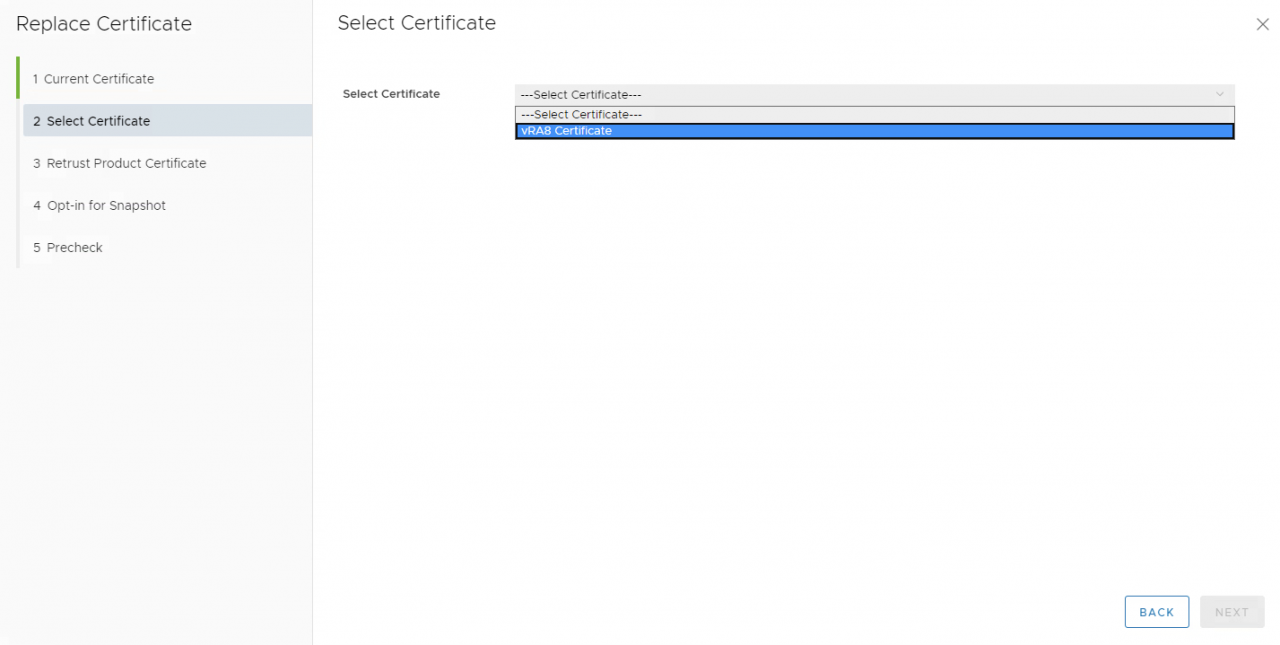
- 在4.Opt-in for Snapshot中,选中
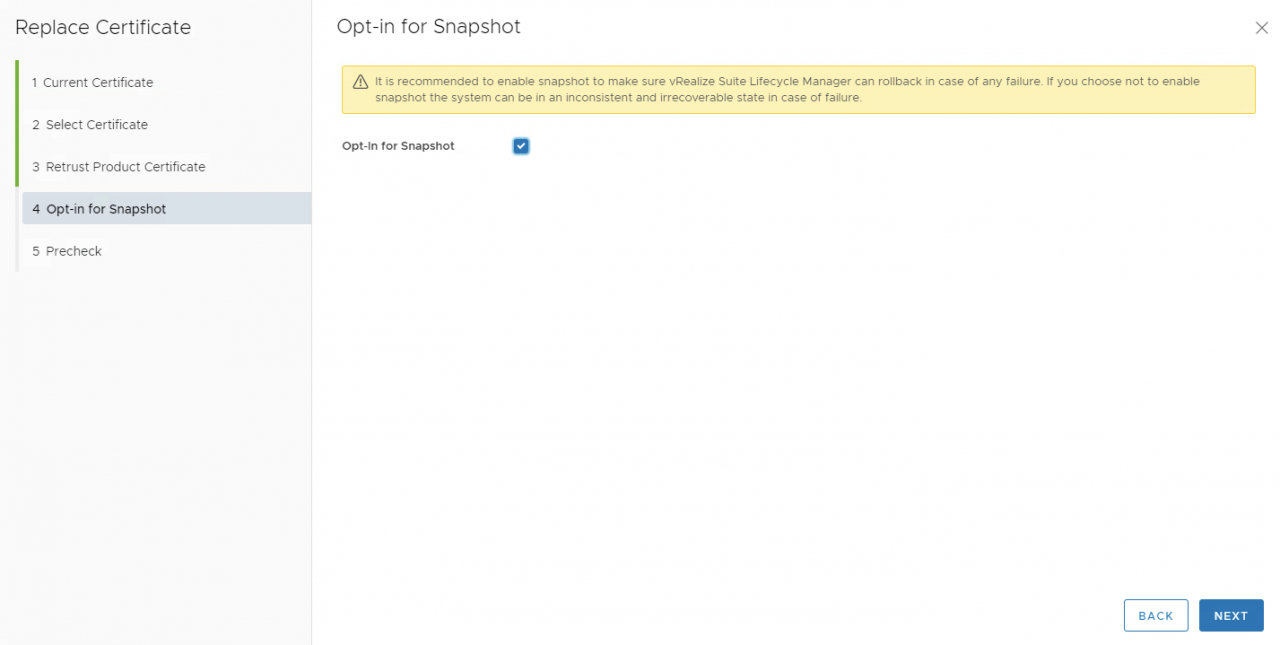
- 在5.Precheck中,点击"RUN PRECHECK",确认无问题后,点击"FINISH"执行证书替换
- 根据环境不同,需等待约20-40分钟完成vIDM证书替换

- 等待vIDM证书替换完成后,重复6-11步,替换vRA8证书
- 根据环境不同,需等待15-30分钟完成vRA证书替换

- 登录vIDM和vRA8验证证书替换后的效果
完成
至此,我们完成了所有vRealize系列产品的证书替换,截止到系列六,VMware核心产品的证书替换已经完成,可以看出,VMware非常重视产品通讯的安全,并提供非常便捷的方式替换证书。