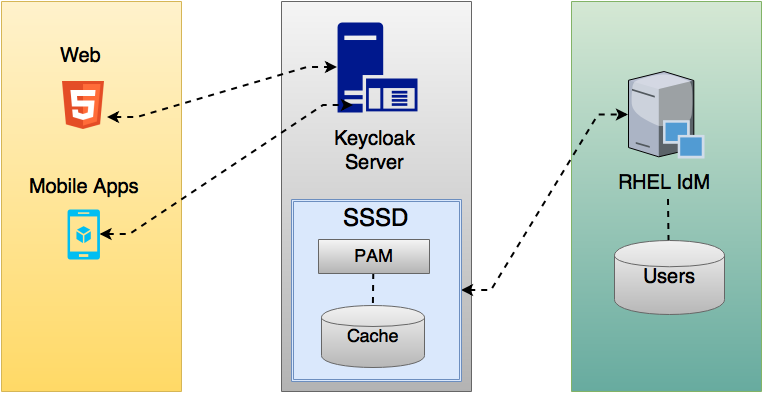
 Keycloak是一个致力于解决应用和服务身份验证与访问管理的开源工具。可以通过简单的配置达到保护应用和服务的目的。是个人非常喜欢的一个认证平台,因为他几乎可以支持所有的认证集成。
Keycloak是一个致力于解决应用和服务身份验证与访问管理的开源工具。可以通过简单的配置达到保护应用和服务的目的。是个人非常喜欢的一个认证平台,因为他几乎可以支持所有的认证集成。
更新系统和基本准备
更新CentOS7系统补丁
yum update -y安装Java8
yum install -y java-1.8.0-openjdk wget创建keycloak用户
KeyCloak不允许root运行
groupadd -r keycloak
useradd -m -d /var/lib/keycloak -s /sbin/nologin -r -g keycloak keycloak配置外部数据库驱动(例如:Mysql、Microsoft Sql Server)
在Microsoft SQL Server中创建keycloak数据库
安装Keycloak
创建软件运行目录
为了方便日后升级,通过软链接管理版本
mkdir -p /usr/local/keycloak/8.0.2
ln -s /usr/local/keycloak/8.0.2 /usr/local/keycloak/current
cd /usr/local/keycloak下载Keycloak软件
wget https://downloads.jboss.org/keycloak/8.0.2/keycloak-8.0.2.tar.gz
tar -xzf keycloak-8.0.2.tar.gz -C /usr/local/keycloak/current --strip-components=1
chown keycloak: -R /usr/local/keycloak配置standalone文件夹权限
因为他包含隐私数据
cd /usr/local/keycloak/current
sudo -u keycloak chmod 700 standalone下载Microsoft SQL Server连接驱动
下载jdbc驱动,并拷贝到文件夹中,稍后进行配置
https://download.microsoft.com/download/4/D/C/4DCD85FA-0041-4D2E-8DD9-833C1873978C/sqljdbc_7.2.2.0_enu.tar.gz
tar zxvf sqljdbc_7.2.2.0_enu.tar.gz
mkdir -p /usr/local/keycloak/current/modules/system/layers/keycloak/com/microsoft/main
cp sqljdbc_7.2/enu/mssql-jdbc-7.2.2.jre8.jar /usr/local/keycloak/current/modules/system/layers/keycloak/com/microsoft/main添加module.xml驱动描述文件
cat > /usr/local/keycloak/current/modules/system/layers/keycloak/com/microsoft/main/module.xml <<EOF
<?xml version="1.0" ?>
<module xmlns="urn:jboss:module:1.5" name="com.microsoft">
<resources>
<resource-root path="mssql-jdbc-7.2.2.jre8.jar"/>
</resources>
<dependencies>
<module name="javax.api"/>
<module name="javax.transaction.api"/>
</dependencies>
</module>
EOF编辑keycload standalone文件夹中的standalone.xml文件
先对配置文件进行备份
cp /usr/local/keycloak/current/standalone/configuration/standalone.xml /usr/local/keycloak/current/standalone/configuration/standalone.xml.bak添加datasource和driver,替换KeycloakDS数据源为sql server的 vi /usr/local/keycloak/current/standalone/configuration/standalone.xml
<subsystem xmlns="urn:jboss:domain:datasources:5.0">
<datasources>
<datasource jndi-name="java:jboss/datasources/ExampleDS" pool-name="ExampleDS" enabled="true" use-java-context="true" statistics-enabled="${wildfly.datasources.statistics-enabled:${wildfly.statistics-enabled:false}}">
<connection-url>jdbc:h2:mem:test;DB_CLOSE_DELAY=-1;DB_CLOSE_ON_EXIT=FALSE</connection-url>
<driver>h2</driver>
<security>
<user-name>sa</user-name>
<password>sa</password>
</security>
</datasource>
<datasource jndi-name="java:jboss/datasources/KeycloakDS" pool-name="KeycloakDS" enabled="true" use-java-context="true" statistics-enabled="${wildfly.datasources.statistics-enabled:${wildfly.statistics-enabled:false}}">
<connection-url>jdbc:sqlserver://10.133.5.37:1433;DatabaseName=keycloak;</connection-url>
<driver>sqlserver</driver>
<security>
<user-name>sa</user-name>
<password>yyfwsqlserver@2012</password>
</security>
</datasource>
<drivers>
<driver name="h2" module="com.h2database.h2">
<xa-datasource-class>org.h2.jdbcx.JdbcDataSource</xa-datasource-class>
</driver>
<driver name="sqlserver" module="com.microsoft">
<driver-class>com.microsoft.sqlserver.jdbc.SQLServerDriver</driver-class>
<xa-datasource-class>com.microsoft.sqlserver.jdbc.SQLServerXADataSource</xa-datasource-class>
</driver>
</drivers>
</datasources>
</subsystem>创建Keycloak默认用户
默认用户用于管理员登录
cd /usr/local/keycload/current
./bin/add-user-keycloak.sh -u admin -p VMware1! -r master创建keycloak系统服务
cat > /etc/systemd/system/keycloak.service <<EOF
[Unit]
Description=Keycloak
After=network.target
[Service]
Type=idle
User=keycloak
Group=keycloak
ExecStart=/usr/local/keycloak/current/bin/standalone.sh -b 0.0.0.0
TimeoutStartSec=600
TimeoutStopSec=600
[Install]
WantedBy=multi-user.target
EOF重新加载Keycloak系统服务
systemctl daemon-reload
systemctl enable keycloak
systemctl start keycloak(可选)Nginx反向代理Keycloak配置
由于Keycloak属于认证系统,要求证书信任,我的环境中使用nginx载入Let's Encrypt证书,所以我会使用反向代理连接keycloak,那么Keycloak就需要进行如下配置修改
sudo -u keycloak ./bin/jboss-cli.sh 'embed-server,/subsystem=undertow/server=default-server/http-listener=default:write-attribute(name=proxy-address-forwarding,value=true)'
sudo -u keycloak ./bin/jboss-cli.sh 'embed-server,/socket-binding-group=standard-sockets/socket-binding=proxy-https:add(port=443)'
sudo -u keycloak ./bin/jboss-cli.sh 'embed-server,/subsystem=undertow/server=default-server/http-listener=default:write-attribute(name=redirect-socket,value=proxy-https)'修改配置后,重新启动服务
systemctl restart keycloak
systemctl enable keycloak(可选)Nginx安装和配置
提前准备好证书,或者使用acme申请免费证书,以下只是示例。
yum install nginx -y
cat > /etc/nginx/conf.d/keycloak.conf <<EOF
upstream keycloak {
# Use IP Hash for session persistence
ip_hash;
# List of Keycloak servers
server 127.0.0.1:8080;
}
server {
listen 80;
server_name my.url.com;
# Redirect all HTTP to HTTPS
location / {
return 301 https://\$server_name\$request_uri;
}
}
server {
listen 443 ssl http2;
server_name my.url.com;
ssl_certificate /etc/pki/tls/certs/my-cert.cer;
ssl_certificate_key /etc/pki/tls/private/my-key.key;
ssl_session_cache shared:SSL:1m;
ssl_prefer_server_ciphers on;
location / {
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_pass http://keycloak;
}
}
EOF
nginx -t
sysmtectl enable nginx
systemctl start nginx访问Keycloak管理控制台
https://my.url.com